IAM Survey
Challenge
Solution
Outcome
The OmniSolve team cleansed and aggregated all of the IAM survey results into a single reporting data set. The cleansing tasks included addressing missing data, errors and anomalies, reformatting issues such as text and numeric formats, adding report categories and classifiers to assist with data mining. Aggregation tasks included focussing on creating a single analytic and reporting data record for each owner-application which could be synthesized and data mined for insights.
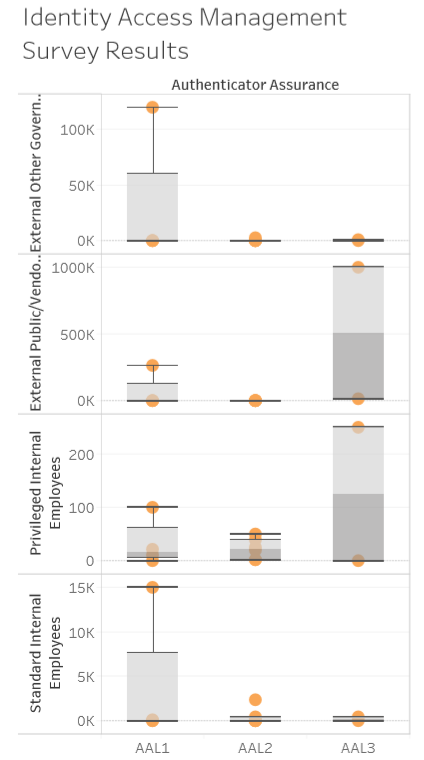
Once the IAM reporting data set was ready, a dashboard was created in Tableau. The Tableau dashboard included visualizations for IAM survey summary results. Visualizations included areas such as,
- Employee and non employee usage counts
- Identity and authentication assurance comparatives
- Top 10 Protocols and entitlement solutions
These profile views allowed the stakeholders in IT security and enterprise architecture teams to develop the current profile and security posture, including gaps in capabilities and duplicative and obsolete technologies.
Technologies & Methodologies
 |
| Tableau |
Featured Experts